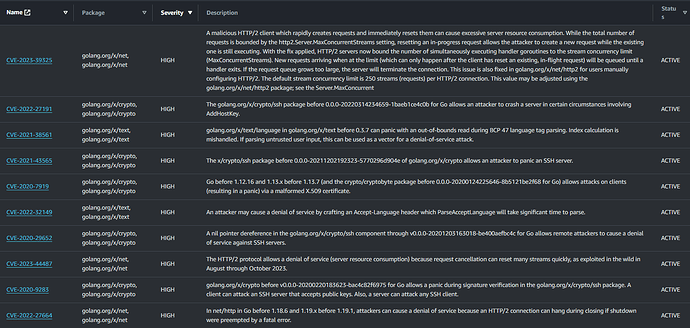
I am not quite sure how to address resolving CVEs that are surfaced by AWS ECR security scans for this “official” docker image (golang:1.22.5-alpine3.20). The CVEs that are reported are asw follows and they appear to be coming from go.mod files in the /usr/local/go/src.
Drilling into the details, I see they all point to the same 3 packages: golang/x/net, golang/x/crypt, and golang/x/text.
One example detail view is like this:
CVE-2022-27191 - golang.org/x/crypto, golang.org/x/crypto
Finding ID: arn:aws:inspector2:eu-west-2:######657:finding/58b03c24c39cde6d8f20e74fd89da72e
The golang.org/x/crypto/ssh package before 0.0.0-20220314234659-1baeb1ce4c0b for Go allows an attacker to crash a server in certain circumstances involving AddHostKey.
Finding details...
Inspector score and vulnerability intelligence
Finding overview
Severity: High
Type: Package Vulnerability
Fix available: Yes
Last known public exploit at
Exploit available
No
Created at: August 3, 2024 10:33 AM (UTC-04:00)
Affected packages
Name: golang.org/x/crypto
Installed version / Fixed version: 0:0.0.0-20191011191535-87dc89f01550 / 0.0.0-20220314234659-1baeb1ce4c0b
Package manager: GOMOD
File paths:usr/local/go/src/crypto/internal/edwards25519/field/_asm/go.sum, usr/local/go/src/crypto/internal/bigmod/_asm/go.sum
Could someone please advise me on how I might remediate these without possibly introducing issues into an “official” release of a Go install? I am reluctant to make changes to this image. We use this image as a docker builder to build our Go applications. Those built applications have no CVEs that show up in a scan. But, our security guys are pinging me about this Go build image with 11 major CVEs. I am also no sure if my application might pick up code from the golang.org/x/{crypt,net,text} from the builder image /usr/loca/go/src Why does an official release even have such included CVEs to start with? I am new to dealing with patching stuff like this so I am sorry if I am asking obvious questions here. Thanks in advance for any help and pointers.